Describe and differentiate audit events and logs for local and AD/LDAP users
If you have enabled Active Directory authentication to manage roles or access in the Prism web console, the AD users might receive the Authentication Failed error message while logging on to the Prism web console.
This article describes ways to troubleshoot such issues and to check what might be wrong in the environment, provided that you have configured LDAP as described in the Configuring Authentication article.
You can run the following NCC check to check for any configuration issues:
ncc health_checks system_checks ldap_config_check
There are many reasons for the Prism login failure using the domain credentials. Check the prism_gateway.log on the Prism master CVM (Controller VM), and search for the username and check the error messages to determine the cause of the failure.
To find the Prism leader, run the below command on any CVM:
allssh jps
Executing jps on the cluster
================== x.x.x.x =================
18289 Bootstrap
7954 HyperintMain
17001 Jps
5162 QuorumPeerMain
The CVM with the ‘Bootstrap’ entry is the Prism leader.
To isolate the issue further, create a test user in the domain with a simple password and test the same.
Following are some of the reasons for the Prism login failure.
- DNS is not correctly configured or is not reachable
- Domain controllers are not reachable or the reachable domain controller has issues
- Username or password is incorrect
- Port number used to connect to the AD is incorrect
- The group name is incorrect because the group name is case sensitive
- Issue with service account configuration
- High latency in logging in to the Prism web console
DNS is not correctly configured or is not reachable
Perform one of the following steps to check the DNS status.
- Log on to the Prism web console, click on the gear icon and check the names in the Nameservers tab, and verify if the servers present are correct.
- Log on to any CVM and ping the DNS servers and also perform an nslookup check to check if they are reachable.
- Ping the domain name (for example, mydomain.local) from the CVM or a domain controller name. This depends on whether you have used a domain controller name or domain name in the Prism configuration.
Domain controllers (DC) are not reachable or the reachable domain controller has issues
Perform the following steps to check the DC status.
- Check if you are able to ping all the DCs by name and IP address.
- Check the subnet of the cluster, and then log on to any Domain Controller and open Active Directory Sites and Services to check the nearest DC to the cluster.
- Log on to the DC by following the preceding step, and check for any issues in the DC.
Username or password is incorrect
As Prism does not support the Windows Authentication format (domain\username) for authentication of users, the UPN format (name@domain.com) is used, which could be the email address or an alternate UPN suffix. In this scenario, the login instantly fails.
Some organizations use alternate UPNs for exchange email address. For example, a directory name is ABC whereas a user can have an email address in the first.last@def.com format where def.com is used for email routing.
To check the preceding, perform the following procedure.
Note: If the UPN suffix is modified to point to a parent or child domain in the Active Directory configuration at any point of time, this change should be reflected in the domain field of Authentication Configuration on the Prism web console for logins to work.
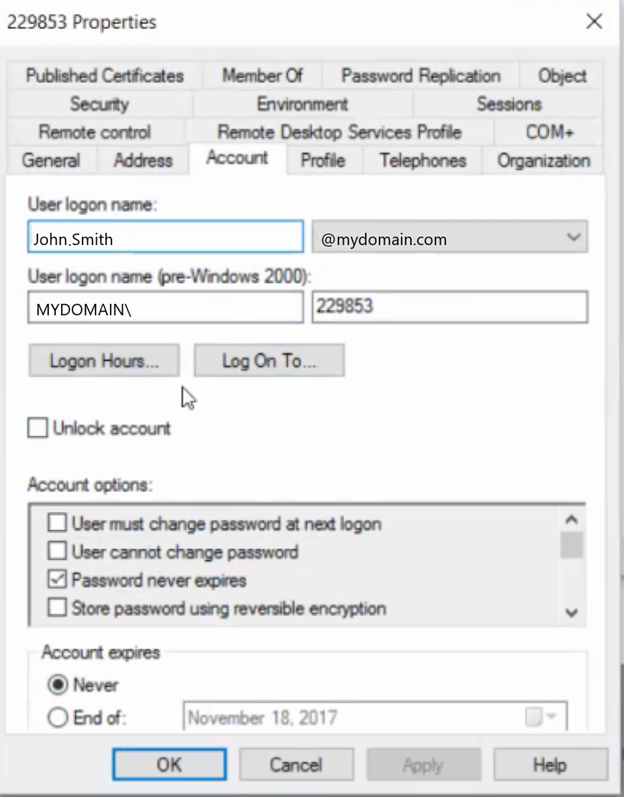
- Go to Active Directory Users and Computers and open User properties, and then go to the Account tab.
- In User Object, check the two User Logon Names.
In the sample screenshot above, the first one is the UPN, which is in the John.Smith@mydomain.com format. The second one is the samAccount Name (pre-Windows 2000), which was originally intended to be used as DomainName\user, which translates to MYDOMAIN\229853. However, in the Nutanix LDAP configuration, the user is able to log in only in the following format: 229853@mydomain.com.
- Check the User Object in the AD configuration, and check if the UPN and samAccount names are the same. If not, the correct way to authenticate a user is by logging in as samAccountName@domain.
Port number used to connect to the AD is incorrect
For example, the supported port such as 389 is not used. For more information about the usage of the correct port number, see Unable to Log In to the Prism web console using Group LDAP authentication.
The group name is incorrect because the group name is case sensitive
If a group is assigned a role, the group name must exactly match the case of the group name displayed in the Active Directory.
Issue with service account configuration
From AOS/PC (Prism Central) 5.5, Nutanix introduced service account for LDAP configuration. This user (with read permission in AD) will validate the login attempts in Prism with AD.
2018-12-20 13:27:08 ERROR ldap_client.py:132 {‘info’: ‘80090308: LdapErr: DSID-0C0903D3, comment: AcceptSecurityContext error, data 533, v3839’, ‘desc’: ‘Invalid credentials’}
2018-12-20 13:27:08 ERROR directory_service.py:658 Failed to get user with username john.smith@mydomain.local from domain mydomain.local, error Invalid credentials for directory url: ldap://xx.xx.xx.xx
2018-12-20 13:27:08 ERROR auth.py:98 Error: Traceback (most recent call last):
File “/home/hudsonb/workspace/workspace/OSLAB_euphrates-5.9.2-stable-release/builds/build-euphrates-5.9.2-stable-release/python-tree/bdist.linux-x86_64/egg/aplos/lib/auth/auth.py”, line 72, in session_authenticate
File “/home/hudsonb/workspace/workspace/OSLAB_euphrates-5.9.2-stable-release/builds/build-euphrates-5.9.2-stable-release/python-tree/bdist.linux-x86_64/egg/aplos/lib/auth/auth.py”, line 184, in validate_user_auth
File “/home/hudsonb/workspace/workspace/OSLAB_euphrates-5.9.2-stable-release/builds/build-euphrates-5.9.2-stable-release/python-tree/bdist.linux-x86_64/egg/aplos/lib/user_management/user_util.py”, line 185, in search_ds_user
File “/home/hudsonb/workspace/workspace/OSLAB_euphrates-5.9.2-stable-release/builds/build-euphrates-5.9.2-stable-release/python-tree/bdist.linux-x86_64/egg/aplos/lib/directory_service/directory_service.py”, line 659, in get_user_from_DS
DsSearchError: Failed to get user with username john.smith@mydomain.local from domain mydomain.local, error Invalid credentials for directory url: ldap://xx.xx.xx.xx
– UWSGI – [GET]:/v3/users/me?_=1545312428525 – took 36 msecs, response status: 500
Below are a few reasons for encountering this issue:
- Configured service account does not have necessary permissions
- Configured wrong user
- Password expired
- Account disabled
- serviceAccountUsername Field is empty [Noticed after upgrade for <5.5 versions]