Explain security concepts such as two-factor authentication, key management and cluster lockdown
Two Factor Authentication
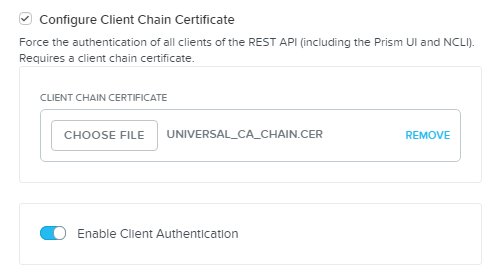
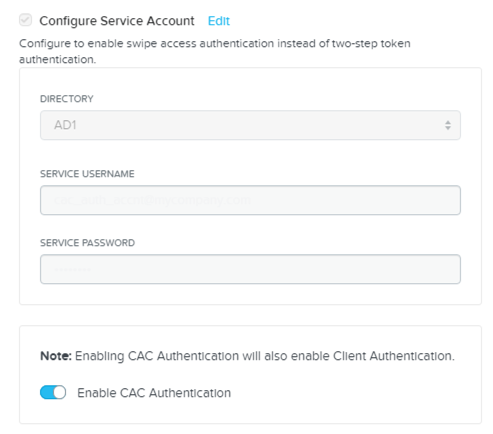
You can enable two-factor authentication for users through a combination of a client certificate and/or username/password to address stringent security needs.
Key Management
Nutanix supports key-based SSH access to a cluster. Adding a key through the Prism web console provides key-based access to the cluster, Controller VM, and hypervisor host. Each node employs a public/private key pair, and the cluster is made secure by distributing and using these keys.
You can create a key pair (or multiple key pairs) and add the public keys to enable key-based SSH access. However, when site security requirements do not allow such access, you can remove all public keys to prevent SSH access.
Cluster Lockdown
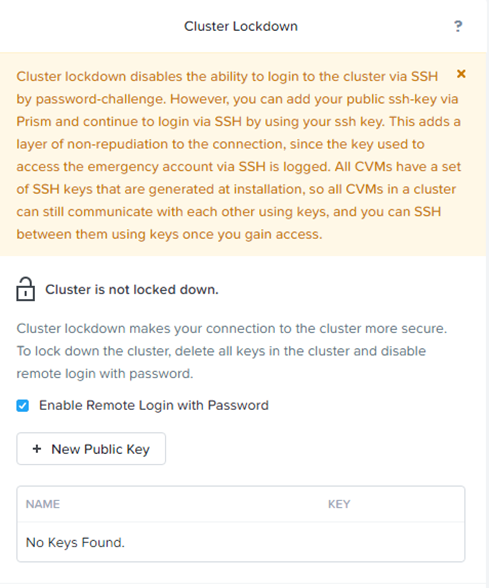
You can easily lock down access to Nutanix clusters if your environment mandates heightened security requirements. Cluster Shield restricts access to a Nutanix cluster by disabling interactive shell logins.
Cluster lockdown is the ability to disable password based CVM access and/or only allow key based access.